Registry Cleaner
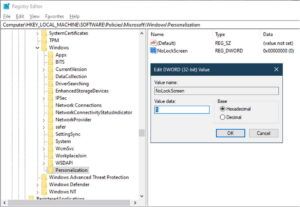
We’ve also included an “EnableFirstLogonAnimation.reg” if you’d like to re-enable it again. While this is a pretty small sample size—and specifically only for new users signing in for the first time—it seems that disabling the animation completely could save a lot of time for new users. This fixed it for us on 1903 as well, went from a 2 min logon time to 44 seconds, with out any optimizations. Originally we used LTSR, but have been experiencing same long logon times in VDA 1903 or 1909. Also, several sections you have the order different for reg.exe add parameters, and some names are in quotes while others are not.
- Additionally Windows 95 backs up the registry to the files system.da0 and user.da0 on every successful boot.
- You can customize the areas you want to scan and also view and unselect entries selected to be deleted.
- Windows registry excels in these scenarios where the application configuration is shared among various users.
S0134 Downdelph Downdelph uses search order hijacking of the Windows executable sysprep.exe to escalate privileges. Adversaries may execute their own malicious payloads by hijacking the search order used to load DLLs. Windows systems use a common method to look for required DLLs to load into a program. Their code can be shared across multiple executables and in return save system resources. DLL files contain an Export Table which is a list of symbols used while being called by a program or other executables. Tech support scams are an industry-wide issue where scammers trick you into paying for unnecessary technical support services.
Computer forensics is the process of methodically examining computer media (hard disks, diskettes, tapes, etc.) for evidence . When considering computer forensics, registry forensics plays a huge role because of the amount of the data that is stored on the registry and the importance of the stored data. The extraction of this data is therefore highly important when investigating. Due to the limitation of tools that can extract forensically valuable data from registry files, investigators have to extract it manually.
Deciding On No-Hassle Solutions Of Dll
A conforming consumer for a JSONrepresentation that is consuming a DID document with a root element that is not a JSON Object MUSTreport an error. A conforming producer MUST take a DID document data model and a representation-specific entries map as input into the production process. The conforming producer MAY accept additional options as input into the production process. The DID document does not express revoked keys using a verification relationship. If a referenced verification method is not in the latestDID Document used to dereference it, then that verification method is considered invalid or revoked.
Explaining Practical Systems Of Missing Dll Files
Though many of these fixes seem simple, you may have to try a few of them in the list because it’s hard to say what’ll work. Certain Windows updates can change or replace .dll files, so these files are not available when another program wants to use them. The upside with this fix is it will improve the overall health of your system as well.
All of our articles are informative visuals and step by step instructions. Read latest technology news, reviews, how-to guides and other tips & tricks covering Windows, Linux, Mac & dllcenter.com/broadcom-corporation Android operating systems prepared by our team.
Registry cleaner software will state that your programs will be confused by the duplicate entries, slowing your machines performance, but that is not true. If you are using an Internet security suite or Firewall software program, try to temporary disable or pause its protection. All antivirus, security suite and Firewall programs allow users to disable their real-time protection.


Leave a Reply