New phishing Exodus campaign targets Chinese crypto investors
Cybersecurity analysts have uncovered a new phishing campaign targeting crypto users by deploying FatalRAT alongside Clipper and Keylogger malware.
Cyble Research and Intelligence Labs have uncovered a novel phishing campaign targeting Chinese crypto investors and organizations, with an emphasis on users of the Exodus crypto wallet.
In a blog article, the cybersecurity experts revealed that unidentified threat actors have employed a fake website designed to mimic the interface of the Exodus crypto wallet in an effort to trick victims into sharing their private information without realizing it.
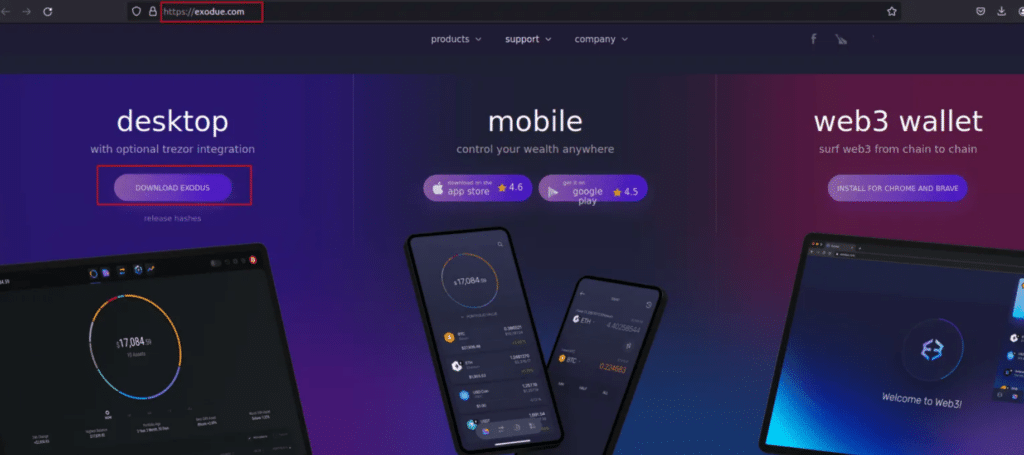
Once unsuspecting users are lured into downloading the software disguised as genuine Exodus installers from the phishing site, they inadvertently install FatalRAT, a type of malware that hackers use to gain control over someone’s computer remotely. Moreover, the program also lures users by starting the Exodus installation, making them think it’s real, while actually diverting their attention to hide its true intentions.
Cyble notes that in addition to the Exodus program, the installer also deploys other malicious components, such as Clipper and Keylogger, programs designed to intercept and modify clipboard data on a victim’s computer. The analysts emphasized that this time, the hackers have employed new .dll side-loading techniques as part of their strategy to evade detection. While it’s not clear how big the attack is, the hackers appear to be targeting Chinese crypto investors and companies with Chinese-language installers, Cyble noted.












Leave a Reply